What quantum computing means for cyber security
An introduction to Quantum Computing, how to use it, impact on common modern cryptographic algorithms and how to mitigate the cyber security risks.

Quantum computing is the next big thing after Artificial Intelligence (AI). Big technology firms like IBM, Google, AWS and Microsoft are pouring huge amounts of effort and resources into bringing the technology mainstream. While quantum mechanics is arguably still in its infancy the underlying principles and ideas have been around for over a century. Progress has been slow but there have been gradual steps in advancement and understanding that have led to the development of much of the modern world and the technology we are dependent on.
This article provides an introduction to Quantum Computing, how to use it, impact on common cryptographic algorithms and how to mitigate the cyber security risks. Like everyone else we are on a learning curve. If there are parts you don't fully understand that's fine, there are lots of unanswered questions - this is leading edge physics and technology and it's harder than rocket science!🚀
What is quantum computing and how to use it
A quantum computer works in a fundamentally different way to a modern classical computer. Instead of working with binary 0 and 1, a quantum computer works with qubits that can be 0, 1 or anywhere in between at the same time. We know that sounds odd but basically quantum computers are effectively in all states at the same time until measured. It’s the act of measuring that causes the quantum effects to disappear (called decoherence) and if programmed correctly provide you with the answer you were looking for.
If you are looking for a good high-level introduction to quantum computing that you would feel relatively comfortable with we would recommend:
For a more detailed background we recommend the following but be warned it’s heavy going on the maths and takes a lot of time and effort to fully appreciate. Understanding Quantum Information and Computation With John Watrous - YouTube
Quantum roadmap
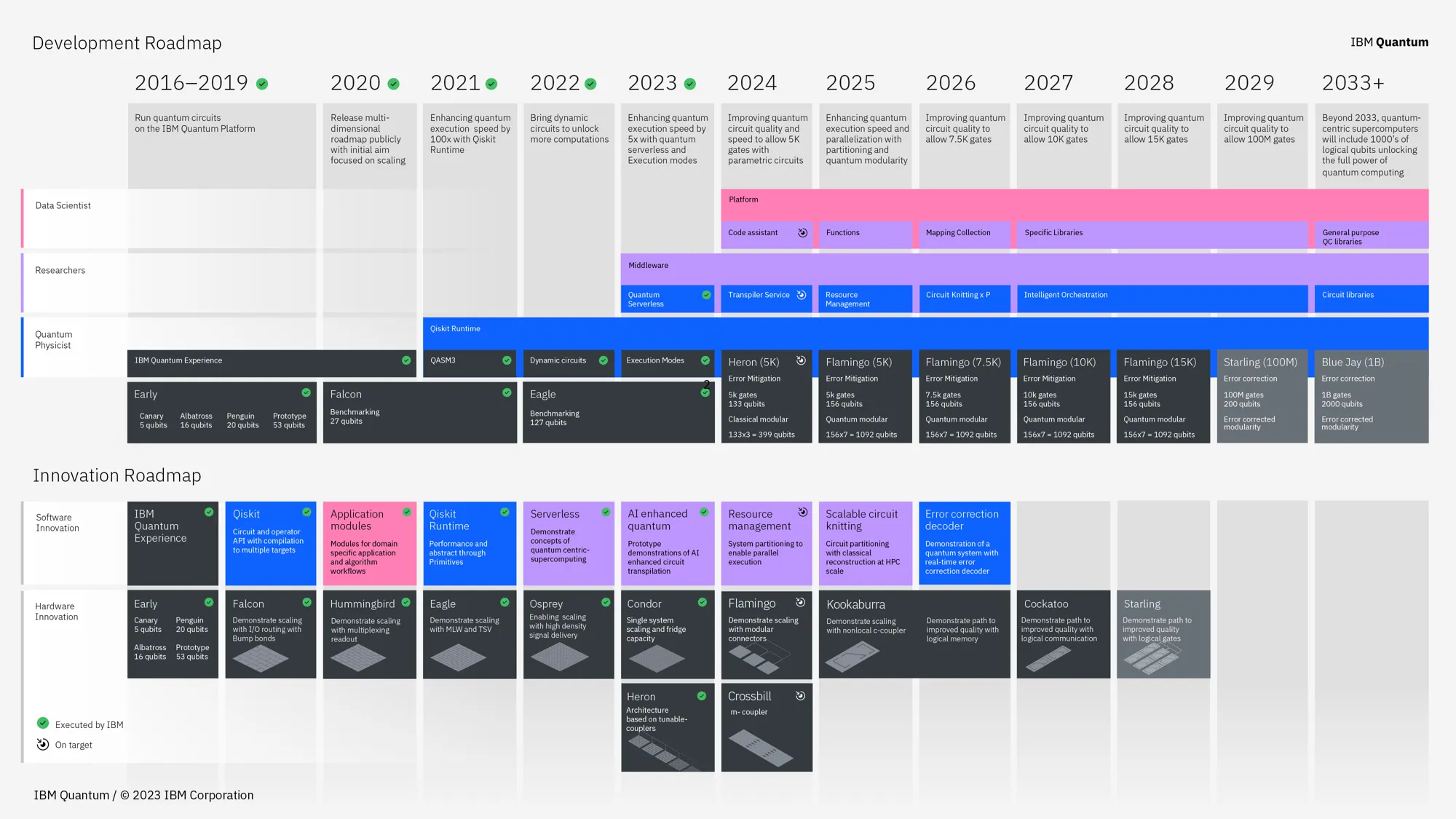
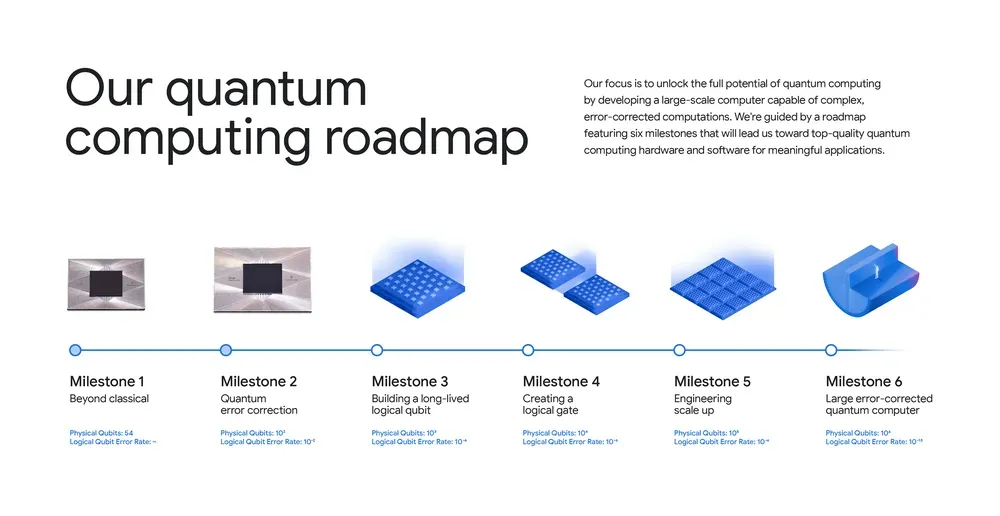
Now you have a general understanding of the subject it's good to have a visual roadmap of where the technology is today and how big technology firms intend to innovate further. If you are more interest in the hardware side of things these roadmaps from IBM and Google may be of interest.
IBM quantum roadmap
Google quantum computing roadmap
What are the benefits
Simply put quantum computers can do things that a modern classical computer cannot. Using 'quantum effects' they allow the solving of more types of mathematical problems and quicker. This will lead to the advancement in most if not all scientific domains including AI, medicine, biology and material science. You should expect it to have a profound impact on technological advancement.
Where is the technology today
Today (December 2024), the technology has the ability to support 156 qubits. This is a very small number and limits what can be usefully done. In order to be more useful, this needs to be in excess of 1000+ qubits. However, it’s not simply scaling up the number of qubits that’s required. The key problem relates to the error rate and as you increase in qubits the error rate increases accordingly. Quantum states are fragile and prone to errors limiting their usefulness. In a recent news release by Google they announced a major break through that enables the number of qubits to be scaled up without the error rate increasing significantly, to further enable practical application of quantum computers in the 'real world' (no pun intended😃).
Link on Google for more information on their Willow quantum chip.
University rollout
Quantum computers are breaking out of tech firm labs into universities. Moving from the domain of tech firms it opens the potential for greater research and development. The first university to purchase a quantum computer was reportedly Chungbuk National University (CBNU) in South Korea. It’s designed and built by IQM a Finnish-German maker of Quantum Computers. The second was reportedly Yonsei University also in South Korea by IBM.
This is just the start and we expect this permeation of the technology to not only continue but accelerate. The rate of technological break throughs in the field of quantum computing is about to accelerate.
How to use quantum computing
When you watch the presentations by quantum physicists it all seems very complicated and difficult. However, we need to draw a distinction between trying to understand the science and using it. Simply put there are software libraries available that allow you to program quantum computers using a modern classical computer. To make this even easier two of the software libraries Qiskit from IBM and Cirq from Google are based on the Python programming language.
IBM: Qiskit
Qiskit allows the programme to be converted to a form that a quantum computer can take as input. The Qiskit Software Development Kit includes all of the necessary components to program a quantum computer including the transpilation which is similar to a compiler but takes the code and makes it compatible with the specific quantum computing device being used. To find out more about Qiskit IBM has produced this seven video series on Coding with Qiskit.
Google: Cirq
Similar to Qiskit Google Cirq is based on the Python programming language. To find out about Cirq Google has produced this five video series on Quantum programming with Cirq.
We haven't attempted to programme a quantum computer yet but when we do we will write another blog - stay tuned!
Impact on common cryptographic algorithms
The key area of concern relating to Quantum Computing is around the use of cryptography. Cryptography is the bedrock of the modern internet and data security. Without trust in the underlying cryptography modern e-commerce will collapse. Cryptography is used to protect communications, protect and confirm your identity, sign documents, grant you access to the right information and allow internet sessions to be securely established. We will cover three key areas of impact:
Confidentiality of stolen data
Ransomware has been a threat to all firms for over ten years. More recently it has involved the exfiltration of data prior to the deployment of the ransomware that encrypts data and prevents it's legitimate use. This means that attackers potentially have access to a treasure trove of corporate information in the form of the exfiltrated data. While most of this information is in cleartext and readily readable the most sensitive may be encrypted.
The introduction of quantum computing could result in this most sensitive of information being rendered readable. While most information would be of little use after several years there is some information that organisation and nation states would like to keep confidential indefinitely.
This type of attack is referred to as ‘Harvest now, decrypt later'. The perpetrators of such attacks tend to be nation states that are more interested in espionage than monetarisation of an attack.
Some researchers have referred to the day when this happens as the quantum apocalypse. While we are sure this will have an impact, we hope the apocalypse is ‘overhyped’. Saying that we have no idea how nuclear launch codes are generated and suspect they may be vulnerable😊 Let’s hope someone has ‘kicked the tyres’ on that system!
Confidentiality and integrity of communications
Most web-based communications are performed over encrypted connections. This means the introduction of effective quantum computing could result in real-time cracking of the protective encryption rendering the communications vulnerable to interception and interference. This would render all ecommerce related sites open to fraud and undermine internet banking. This single issue could undermine the basis of the information age, destroy trust in online businesses and trust in the global financial systems.
Identity and access control
Cryptography is not only used for confidentiality and integrity but identity. Most identity systems use cryptography for validating identities, signing documents and storing credential information securely. These cryptographic algorithms have been around for a very long time and most are still secure even today. Quantum computing will change that. It will mean that those passwords when stolen, even if encrypted and highly complex, can be read by an attacker and used to launch further attacks on other services where credentials have been re-used. This combined with predicting pseudorandom session IDs will put web based applications and sessions at great risk of hijacking or compromise.
How to mitigate the cyber security risks
There are algorithms that are specially designed to prevent a quantum computer of the future from cracking it. The National Institute of Standard and Technology (NIST) has selected four algorithms to be part of their post-quantum cryptographic standard. More algorithms may be added later. But for now, there’s one for general encryption called Crystals-Kyber and for digital signatures Crystals-Dilithium, Falcon and Sphincs+. These algorithms are called Quantum Safe. NIST has issued some guidance and help on Quantum Safe Cryptography.
Cryptographic asset management
The first place to start is establishing an asset inventory of where you use cryptography. This should uniquely identify the asset, the type of cryptography used, how vulnerable you consider it and the importance of the system concerned. For example, if the system supports your HR team, fund transfer or client financial transactions it may be top of your list of priorities. Remember not to forget any systems that rely on pseudo random number generators including web servers.
Next you should establish a similar inventory but this time of your third party suppliers providing technology services. Again, you should prioritise the list.
Security programme
Once you have your two asset inventories you need to establish a security programme to focus on your priorities. The security programme will decide on the action to take for each vulnerability which could either be to replace with a quantum safe algorithm, increase the key space of the algorithm in place (as a short term mitigant) or to stop using the service altogether.
As part of the programme it is important that new systems and services are quantum safe by default. This means that the change control and release management processes needs to ensure compliance to avoid additional work in the future.
Conclusion
We expect, practical and useful, Quantum Computing to be in general use by the end of the decade! If you haven’t started to move to ‘quantum safe cryptography', we recommend you get moving or you will be left behind and vulnerable.
If you need help moving to Quantum Safe Cryptography please get in touch. We can help you develop a company wide approach that will enable you to track your progress over time with regular checkpoints to encourage greater compliance. This is an activity that will take a long time to implement so the sooner you start the sooner you can achieve Quantum Safety.
About IT Security Locksmith
IT Security Locksmith specialises in board level training and consultancy.
To find out more about our capabilities please click here.
Our services page showcases the types of services we offer.
Click here to contact us for a no obligation initial consultation.
#QuantumComputing #PostQuantumSecurity #CyberSecurity #QuantumSafe #Cryptography #QuantumApocalypse
