How to protect against hackers
An overview of the threats companies face and how those threats ultimately compromise companies. IT Security Locksmith provide a Board Level Trusted Advisor Practical Cyber Security course to help senior executives understand this complex subject in easy-to-understand plain English.

Protecting a network or a system against hackers is challenging. In this article on “How to protect against hackers” I will explain using easy to understand language how to go about it.
Understand where your defences are?
If you haven’t read my blog on How do I improve my company’s cyber security I’d recommend you start there. It will help you understand your strengths and weaknesses.
Understanding who the hacker are?
If you are going to fight a battle it is important to know everything there is about your adversary to give yourself the maximum advantage. We will start by looking at the different types of hacker, what motivates them and their level of sophistication.
Nation States
These are the most sophisticated and motivated. If you are targeted by a Nation State actor you will need to take a long term view of managing them. They will initiate a campaign of activity targeting your company or network and persist until either priorities change or they achieve their aims through a different means. This type of attacker generally does not disclose the breach, they cover their tracks and sometimes plant evidence to mislead you into believing another group attacked you.
Organised Crime
In some countries Nation States and Organised Crime are difficult to distinguish between. This means that these groups are also sophisticated and use some of the techniques and tactics of Nation States. These groups are motivated by monetary gain. The creation of Crypto currencies like BitCoin enabled this particular group to flourish online due to it’s decentralised design, anonymised use (to an extent) and ability to electronically transfer money without involving banks. These groups will slowly leak your data for maximum embarrassment to encourage you to pay the ransom.
Lone wolf and opportunists
These are individuals with the variable levels of skills to probe companies on the internet looking for weakness or vulnerabilities. Your company may not be a specific target but if you have a weakness they are looking for you may become the target. If your cyber security posture looks weak they will devote more time to testing your defences.
Hacktivists
This group are usually motivated by a particular grievance or a specific belief and will target a company accordingly. Similar to Nation State actors these are generally campaign driven which means that while they are much less sophisticated they are persistent. This requires you to ‘keep your guard up’ at all times.
There are numerous companies that can help with providing you with this information referred to as Cyber Threat Intelligence such as Recorded Future. Microsoft also provide this sort of information. If you are using their M365 platform under M365 Defender Threat Analytics is a good place to start.
The 7 stages of a cyber attack
In 2011, Lockheed Martin Corporation developed a very well-known model for a cyber security defence. It’s called the LockheedMartin Cyber Kill Chain(R).
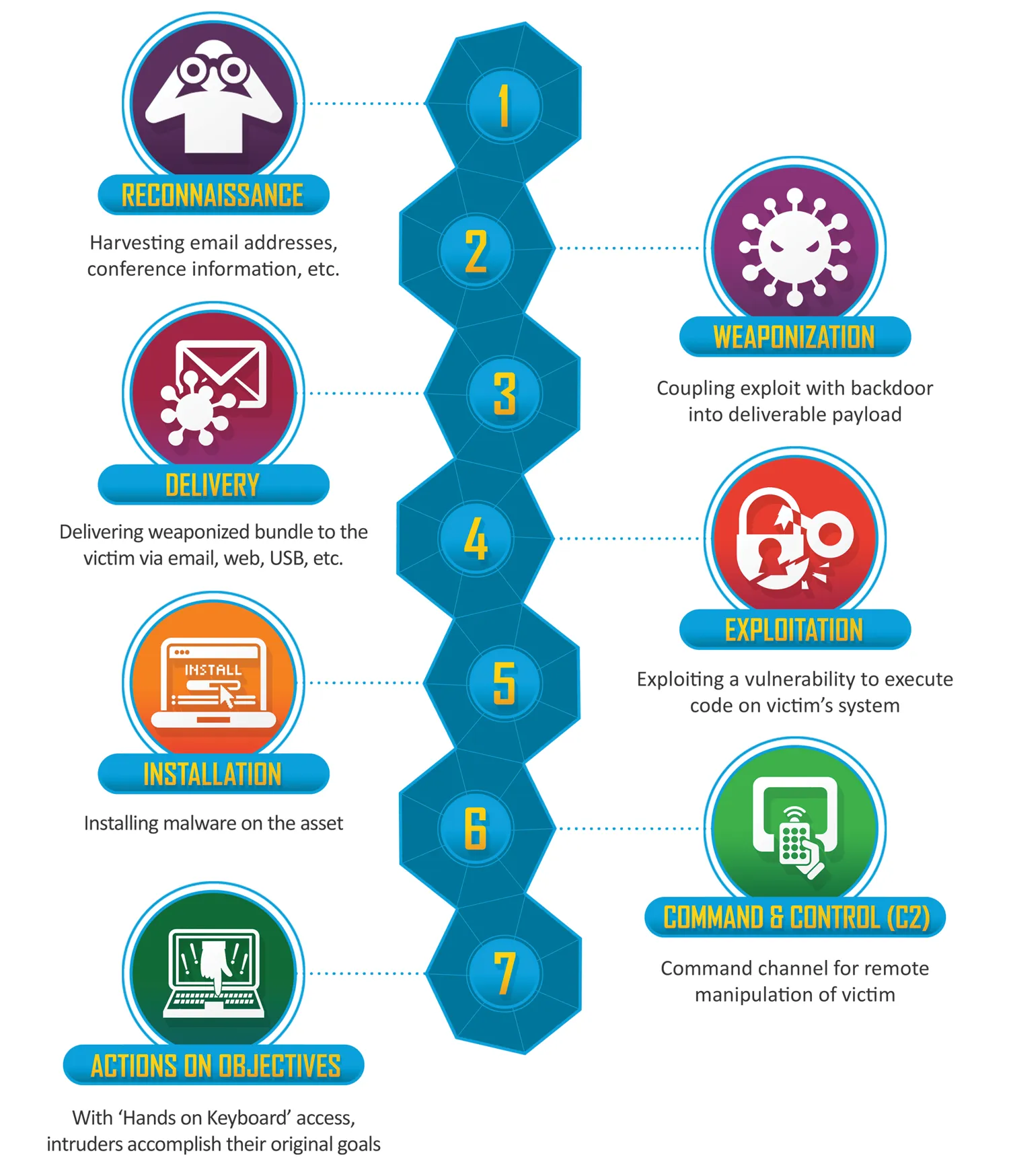
The seven stages in the Lockheed Martin Cyber Kill Chain are:
1. Reconnaissance
2. Weaponization
3. Delivery
4. Exploitation
5. Installation
6. Command and Control
7. Actions on Objectives
Reconnaissance
This is self-explanatory and it means the hacker will find out as much about your company, network, systems and people as possible. They will use Open-Source Intelligence capabilities to help them automate this activity.
Weaponization
Sounds like something out of an action-packed movie but it means embedding a malicious program inside a suitable file such as a Microsoft Word or PDF document. When the file is opened the malicious payload is first run and then the document opens as usual.
Delivery
The weaponized file now needs to be delivered either via USB, Email or Web to the intended target.
Exploitation
In order to be highly effective, the embedded malicious program need to exploit a vulnerability in the target system. These are usually unpatched vulnerabilities, misconfigurations or even zero-day exploits. A zero-day exploit is a new vulnerability that isn’t known to the software vendor such as Microsoft and can be used to compromise any targets using the operating system. Such zero-day vulnerabilities are highly sought after and very valuable both to hackers and defenders.
Installation
Following exploitation, the malicious software is installed on the target system.
Command and Control
This means establishing back channels to the hacker to enable remote control of the target system and further compromise of the network.
Action on objectives
Depending on the type of hacker they may perform various actions ranging from copying your data to stealing it and ultimately preventing you from accessing it.
Disrupting the cyber kill chain
Now you know more about the different type of hackers and how they achieve their objectives you can start to think about your own company’s capabilities and how to disrupt the Cyber Kill Chain.
1. Identify any potential groups that are targeting you and perform research on their techniques, tactics and procedures (TTPs)
2. Look at how to improve your company’s cyber security
3. Think about each stage of the cyber kill chain and how to disrupt it
How can IT Security Locksmith help?
This short article provides a very basic overview of the threats companies face and how those threats manifest themselves to compromise companies. IT Security Locksmith provide a Board Level Trusted Advisor Practical Cyber Security course to help senior executives understand this complex subject in easy-to-understand plain English.
Course Outcomes
1. Understand key cyber concepts
2. Better understand the cyber kill chain
3. Appreciate the stages of cyber incident response
4. Have a draft plan for how to recover from a cyber incident
The course has a number of demonstrations that will help drive home the concepts and lessons to be learnt.
Course Delivery
The Board Level Trusted Advisor Practical Cyber Security course is only run four time per year, over two mornings sessions and is limited to 5 attendees maximum. This is to ensure focused delivery and maximise the benefits for attendees and presenter.
Getting in touch
If you have any enquiries or require more information on the course and scheduling, please email: contact@itsecuritylocksmith.co.uk.
