How do I improve my company's cyber security?
An overview of three methods to improve a company's cyber security depending on your current level of maturity.
Cyber Security is a subject that confuses or worries a lot of people. In this article on "how do I improve my company’s cyber security" I will explain in plain English the steps required. Most of the confusion comes from uncertainty, doubt and the use of highly technical jargon and acronyms – there’ll be none of that here.
What are the distinct parts to Cyber Security?
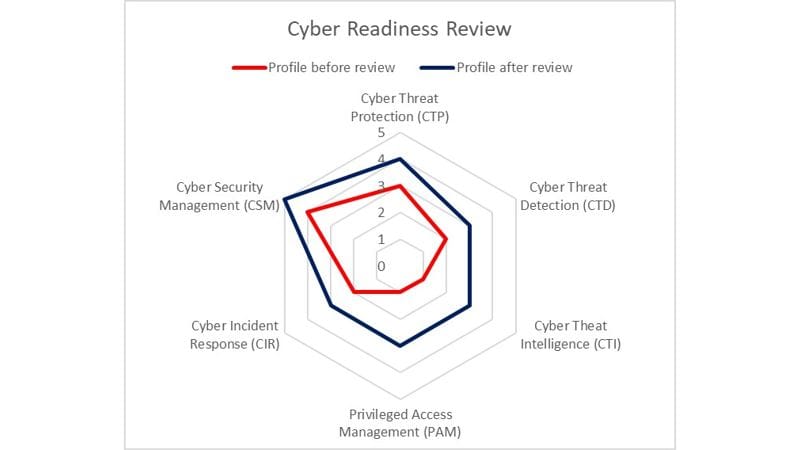
Let’s start with Cyber Security and what are the main parts. In simple terms there are six distinct parts:
• Cyber Threat Protection: stops bad things happening e.g. anti-malware
• Cyber Threat Detection: detects bad things happening e.g. security monitoring • Cyber Threat Intelligence: alerts you to bad things that could happen and what to do e.g. details on attackers and how to mitigate them
• Privileged Access Management: more protection around your admin accounts
• Cyber Incident Response – defines what you do when (not if) you are attacked
• Cyber Security Management – everything else that’s needed to support the above
How to approach cyber security?
This really depends on your business, where you are on your cyber journey and the risks you face. Is your cyber security non-existent, immature or well established? Are you being targeted as part of an ongoing campaign to breach your network or are you simply looking to improve your security before you become a target?
If you have immature cyber security

If your company has an immature approach to Cyber Security then a good place to start is the National Cyber Security Centre. The NCSC has produced a the 10 Step to Cyber Security that companies start the journey of cyber security.
If you are being targeted by cyber attacker
If you are actively being targeted then you may want to take a more practical approach and review key aspects of your cyber security posture. This would mean undertaking a Cyber Threat Intelligence review to determine who is likely to be attacking you and then taking steps to mitigate that threat. This would involve:
• Applying patches to systems that are actively being exploited
• Configuring your systems to be as hard to compromise possible
• Updating your detection systems such as anti-malware and firewalls to detect specific attacks
• Improving your security monitoring capabilities
• Reviewing your cyber security incident response plans also called playbooks
If you have well established cyber security
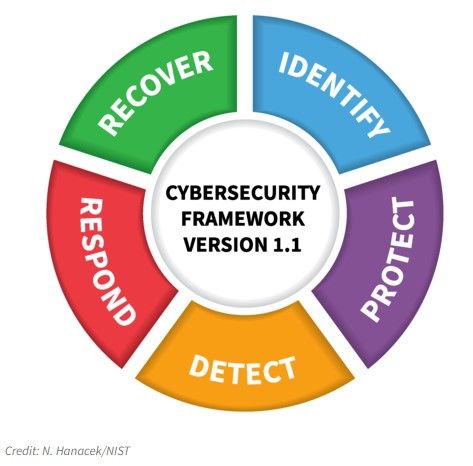
If your company has an established cyber security capability a good way to help improve further is the NIST Cyber Security Framework.
The NIST Cyber Security Framework will allow you to:
• Understand you current cyber profile
• Document the risks you face as a business
• Define you target cyber profile
• Analyse and identify the gaps
• Prioritise you actions to mitigate risks
It sounds simple but there is a lot of work and effort required here to document each step.
How can IT Security Locksmith help?
IT Security Locksmith offer the following services to improve cyber security:
• Cyber readiness review: designed for companies being currently targeted. Aims to quickly improve the basic aspects of your cyber security posture
• Cyber tactical review: based on the NCSC 10 Steps to cyber security.
Aims to document where you are in terms of readiness, analysis of the risks and prioritise next steps
• Cyber strategic review is based on the NIST Cyber Security Framework or similar and aims to document your current level of readiness to map the steps required to improve you cyber security maturity.
It is worth noting that while these steps will improve your cyber security processes it is not replacement for independent technical security testing and ongoing Cyber Security Reviews of systems and technology management (more on these in future blogs).
Getting in touch
If you have any enquiries or require more information, please email: contact@itsecuritylocksmith.co.uk.
