How to fix security vulnerabilities
Simplify and automate vulnerability management to reduce cyber risk. Improve reporting, patching, and governance across your business.

Security vulnerability management is partly a science and partly an art where interpersonal skills are critical. Its why so many companies struggle with it even though they’ve invested in the technology to deliver it. Threat and vulnerability management (TVM) forms part of a Cyber Security Elastic Defence (CSED) along with Cyber Threat Intelligence, Privileged Access Management, Cyber Incident Response and Cyber Threat Protection. It forms a key part of Cyber Threat Detection.
The challenge
There are various challenges with TVM but in most instances companies that struggle will suffer from a combination of:
- Excessive complexity:
a. Too many end points (computers) and poor asset management
b. Too many users and poor user administration
c. Too much software and no software lifecycle management - Uncontrolled privileged access
- Lack of centralised and automated software management
- Ambiguous or no software ownership
- Untargeted and ineffective reporting
Helping the managers manage
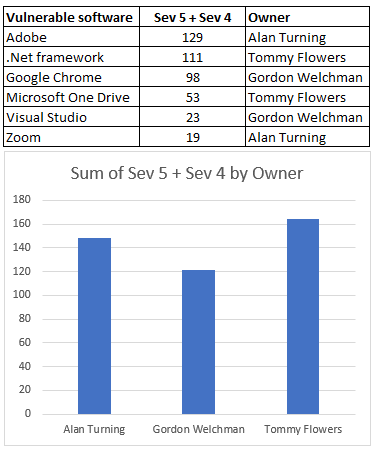
The first thing that needs to be done is to improve the reporting. This means providing real time dashboards for key managers to enable and support them. If they do a good job it’s obvious for everyone to see. Most managers simply want to do a good job and putting in a system with targeted reporting helps them (and you) measure their performance. You can also think about putting in staff performance objectives based on the TVM metrics.
Getting the supporting processes right
Poor asset management, user administration, software lifecycle management and privileged access management processes can severely undermine Vulnerability Management. It is important that someone is accountable and responsible for each one of these areas to improve management control. Improving these processes will indirectly impact the TVM reporting figures over time.
Automation is King
In addition to processes, it’s important to use the right technology to help, this means investing in system patching to ensure you can deploy patches quickly and with as much automation as possible. Any bottleneck in patching systems will result in a cumulative failure over time and a continuous cycle of deteriorating results. Where possible use Microsoft Store to install software as it will help update and maintain it in the future automatically.
Invest in people
It is important to recognise that over time there will be increased pressures on various IT teams as issues come in to focus. These teams may require short term contractors to help them get over the bump in workload and allow them to positively re-enforce their improving patching numbers. It will get easier as the situation improves and unnecessary software and services are removed or disabled.
Patching deployment rings
As with all major change it’s important to test your updates before wider deployment. It also helps the managers responsible for software updates to have confidence that after the pilot group and the initial testing group the update is ready for deployment to the business in a phased rollout. It is very important that the pilot group and initial testing groups are big enough to identify any incompatibility with applications supporting critical business processes. Your Business Continuity Planning should help here.
It’s also critical for senior management to understand that with such change there is an increased risk (albeit controlled) of operational disruption and that this is the cost of improved cyber security.
Complexity is the enemy of vulnerability management
A little dramatic perhaps but complexity is the cause of stressful decisions and ultimately vulnerabilities. By simplifying your environment you will make it easier and more straightforward to patch and update systems.
Standard Operating Systems
By having standard operating systems with agreed configuration profiles for systems hardening will make your job much easier. At every opportunity look to eliminate non-standard systems from your environment. Put controls around change control to only permit authorised Operating Systems to be installed and make it difficult to install anything 'non-standard'.
Central Software Repository
A central software repository with strict control over additions and removals will ensure only authorised software is available for deployment. There should be a regular review of software to eliminate duplication and by implication reduce the licensing costs. Reports covering vulnerabilities in authorised software should be produced at least weekly and shared with software owners.
Cyber Threat Intelligence
Up until this point it’s been a target ripe environment which means there were so many issues and vulnerabilities it was making targeting difficult. Once you get to a relatively compliant level of vulnerability management you should consider bringing you processes into line with Cyber Threat Intelligence. This means rather than simply using vulnerability severity to drive reporting you use other metrics and in particular if it’s being exploited in the wild. These should be your top cyber security priorities going forward. The other reporting still needs to be done but it’s more routine and from a security perspective the reporting you are really interested in is the Cyber Threat Intel through the lens of Vulnerability Management. This allows you to consider the Cyber Threat Protection controls and the Security Monitoring that may help block and detect major threats in the future.
How can IT Security Locksmith help?
IT Security Locksmith offer the following services to help improve your Threat and Vulnerability Management:
A short engagement to review of current mode of operation to make recommendations for future improvements and enhancements
A three-month+ TVM manager coaching and support program (two mornings per week) to help support the TVM manager to implement improvements identified
Please note these services are technology agnostic and the coaching is based on the security management of vulnerabilities rather than configuration of systems and technologies.
I hope you have found this brief article useful and that it has inspired you to have another go at that difficult challenge you’ve been avoiding or struggling with. Good luck.
About IT Security Locksmith
IT Security Locksmith are a cybersecurity company that specialises in board level training and consultancy.
To find out more about our capabilities please click here.
Our services page showcases the types of services we offer.
Click here to contact us for a no obligation initial consultation.
