EU Threat Led Penetration Testing (TLPT)
A short article designed for board level consumption explaining Threat Led Penetration Testing both in terms of key teams and the overall process.
Most companies concerned about their cyber security will be undertaking penetration testing of some sort. This usually involves hiring an external tester to test the security of a given system. So far so simple. This gives you confidence in the security of the system to withstand cyber attack right? Wrong! It does give you a degree of confidence, but you should not assume you are bullet-proof.
This is where threat led penetration testing comes in. Standard penetration testing is predominately focused on testing of systems and is relatively straight forward. TLPT on the other hand is not limited to just the systems but the wider environment including the people using the system and how they interact with it.
Threat led
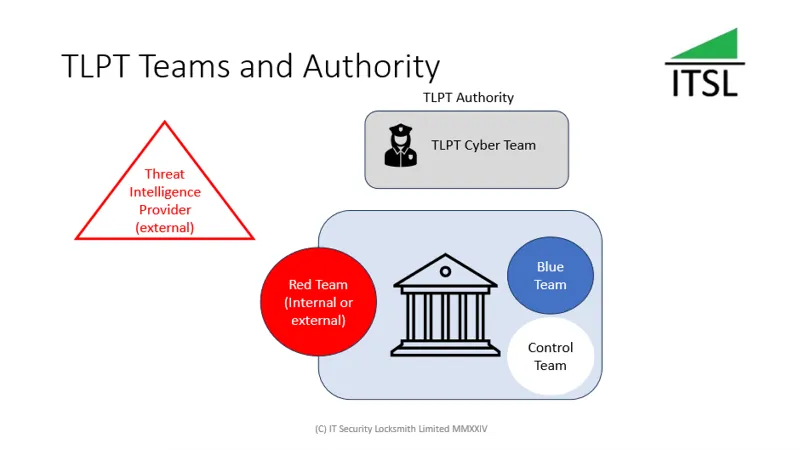
Threat led penetration testing includes a threat intelligence phase. Threat intelligence looks at a number of factors (below) to help develop scenarios to test.
Threat intel factors:
- Employee usernames and passwords (reported in breaches)
- Technical reconnaissance and identification of software or services used
- Staff social media posts and any other information on the web
- Potential physical targeting of premises
- Threat profiling of potential threat actors and their modus operandi
The threat intelligence phase enables threat scenarios to be developed and those with the highest severity score being the most likely to succeed.
Blue team
The blue team, in the field of Cyber Security, is the defending team. They are generally the IT Security or Cyber Security team and more specifically the SOC or Security Operations Centre. Their job is to defend their company and specifically the critical systems and services from cyber attack.
Red teaming
Red teaming is penetration testing where the company defenders, the blue team, are not informed of the test in advance. The red team are generally external testers with a specific set of skills and capabilities. In the case of threat led penetration testing the red team will use the threat scenarios developed through threat intelligence phase to slowly, methodically and stealthily test the company, people and systems. This approach is required to thoroughly test without the blue team being alerted to the attack. It's designed to mimic a real world cyber attack.
Control team
The control team, sometimes referred to as the white team, coordinate the testing. Their job is to keep the test on track without escalation to external parties and law enforcement. They are not permitted to inform the blue team that a test is in progress. As part of the red team test plan, if required, the control team will provide a "leg-up" to enable the remaining test activities to be carried out and tested. All "leg-ups" provided are to be documented in the red team report.
TLPT Authority and Cyber Team
The TLPT Authority is usually a single public authority in the financial sector responsible for all tasks under article 26 of the EU Digital Operational Resilience act (DORA). Within the TLPT authority will be the TLPT Cyber Team. These are the staff responsible for TLPT-related matters. It is up to the TLPT authority to notify a financial entity if a TLPT is required.
If you operate in more than one member state of the EU there may be multiple TLPT authorities but only one will be in overall control of a TLPT test.
EU TLPT
The EU TLPT, which forms part of the DORA Advanced digital operational resilience testing takes a long time to conduct and is not cheap. The EU documentation refers to three stages preparation, testing and closure. However, there are two additional stages not explicitly included in the process that need to be factored in: pre-planning and attestation.
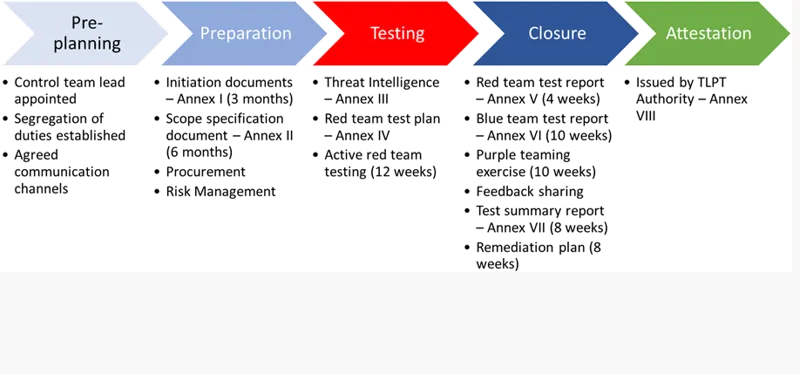
Pre-planning
This stage requires the company to think about documented procedures around threat led penetration testing and the need to assign an individual to the role of control team lead. The procedures will document who will be included in the wider control team and aware of the TLPT. At this stage it is also worth documenting the agreed communication channels to be used to ensure the test remain confidential and not shared with anyone else including the blue team. It’s good to carryout this stage when there's no pressure and you haven’t been notified a test is required. It’s also important to establish working relationships with threat intelligence providers and red team testers in case you require their services.
Preparation
This stage is initiated when you have been informed by the TLPT authority that a test is required. You then have three months to provide the initial document providing basic information and six month to provide a more detailed scope. Both dates are from the TLPT notification date. The initial document will assign a project name which the test will be known by to help avoid tipping off the blue team if they overhear conversations or see documentation. This stage includes procurement of threat intelligence services and red teaming. A final step is to conduct a risk assessment of the testing to mitigate risks and put in place contingency plans. You will be testing live production systems and issues do occur which need to be managed.
Testing
The testing phase will take at least three months. This should immediately tell you that this test is expensive in terms of the cost and the resources. It starts with the Threat Intelligence Report (TIR), then the development of the red team test plan and finally the twelve weeks of testing.
Closure
The closure phase will take at least a further two and a half months. This includes reports from red and blue team, a combined purple team exercise designed to share lessons a summary report to be shared with the TLPT authority and remediation plan.
Attestation
This is completed by the TLPT authority and confirms that the test was carried out according to the regulation.
Financial entities in scope
Not all financial entities are required to undertake TLPT under the EU Digital Operational Resilience Act. The supporting policy document helps to clarify who is in scope in Article 2 on page 30.
It details the types of entities in scope and their characteristics. However, even if you meet this first level of criteria you still need to be assessed by the TLPT authority for “impact-related & systemic character" related factors and ICT risk related factors only then are you potentially “in scope”.
It is worth noting that the TLPT authorities have a large number of financial entities to review and assess. This means even if you are "in scope" it may be some time before they notify your especially given how long these Advanced Tests take.
Conclusion
Threat led penetration testing takes a long time (over six months) to conduct and is expensive of that there is no doubt. The time and effort required to support a TLPT is significant. Companies that undertake this level of advance testing know more about their systems, technology and their blue team. All of which are left enhanced through improved monitoring, detection and the skills learnt. In short, they have improved resilience by undertaking the test and learning from the experience.
Even if you are not in scope for TLPT it is still worth preparing and even carrying out your own red team exercise purely because it will reduce your ICT Risk and improve your digital resilience.
How IT Security Locksmith can help
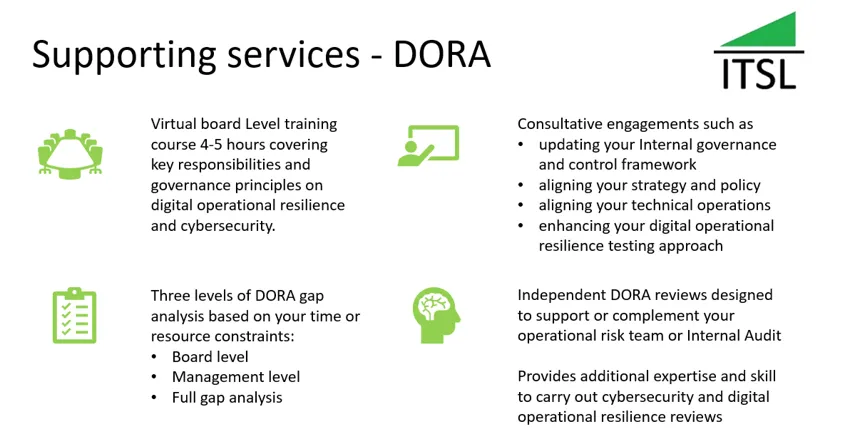
If you need to undertake an EU Digital Operational Resilience Act GAP analysis please get in touch. We offer three levels:
- Board level - takes about three weeks to complete
- Management level - takes about six weeks to complete
- Full gap analysis - takes about three months to complete
Free expert opinion!
If you are concerned about the EU DORA or told that it's all under control please get in touch for a no obligation free consultation. We can help you understand the challenges, how to go about addressing them and provide you with options and prices for you to take away and consider.
If nothing else you get some expert opinion free of charge!
About IT Security Locksmith
IT Security Locksmith are a cybersecurity company that specialises in board level training and consultancy.
To find out more about our capabilities please click here.
Our services page showcases the types of services we offer.
Click here to contact us for a no obligation initial consultation.
