How to meet the EU Digital Operational Resilience Act (Dora)
EU regulators can summons financial services boards, temporary or permanently shut down a financial entity's operations or publicise any breach.

For those of you working in Financial Services that have not read this new piece of EU legislation - it’s huge. Comprising of over 60 Articles and covering a range of disciplines from Information and Communication Technology (ICT) Risk to Physical Security and Crisis Management etc. Books have been written on each one of these topics which gives you a sense of a scale of the challenge. You should not underestimate how long it will require to meet this Act.
“It aims at strengthening the IT security of financial entities such as banks, insurance companies and investment firms and making sure that the financial sector in Europe is able to stay resilient in the event of a severe operational disruption.” Quote from European Insurance and Occupational Pensions Authority.
You can read the full Digital Operational Resilience Act here!
This article will highlight our key points covered in the Act.
Administrative Penalties
To focus our attention let’s start with Article 50, Administrative penalties and remedial measures. In brief, the Act provides many provisions, the three most impactful are:
- “summoning representatives of the financial entities for oral or written explanations on facts or documents relating to the subject matter and purpose of the investigation and to record the answer”
- “require the temporary or permanent cessation of any practice or conduct that the competent authority considers to be contrary to the provisions of this Regulation and prevent repetition of that practice or conduct”
- "issue public notices, including public statements indicating the identity of the natural or legal person and the nature of the breach”
Board Level Governance
The three points above mean that regulators can summons financial services boards to explain their actions (or inaction), either temporary or permanently shut down a financial entity's operations or publicise the fact that you have been in breach.
Compliance with the Act takes effect on January 2025! Giving boards twelve months, from the 17th January 2024, to get a grip on the requirements of the Act and ensure compliance. This means:
- Setting the tone by increasing awareness of the Act and what it means
- Providing direction in terms of Digital Operational Resilience Strategy
- Reviewing capabilities and resourcing across a range of disciplines
- Undertaking independent verification of measures
- Receiving external expert opinion
Internal Governance and Control Framework
It is very important for boards to have a clear understanding of the Internal Governance and Control Framework and its components including level of authority required. The Act applies to the following Internal Governance and Control Framework components:
- ICT Risk Management Framework
- Digital Operation Resilience Strategy
- Information Security Management
- ICT Policy
- Physical security
- Business continuity and crisis management
- Third party management
- Audit Policy
- Communications plans
Implementation planning
The good news is that most financial entities, we expect, will already be doing all of these to some extent. The Act will ensure they are performed to meet the Act’s requirements and sets a bar accordingly. This will no doubt require some financial entities to expand their range of capabilities, hire more staff or to improve their internal processes and systems.
Financial entities should have conducted a gap analysis of their internal capabilities, frameworks, policies and procedures against the Act. It is important that this is supplemented with evidence to demonstrate compliance. Given the size of the Act and the complexity of most financial entities this is a large undertaking and will take a number of months to complete. A gap analysis will give an initial indication of the level of compliance and what's outstanding.
Digital operational resilience strategy
Once you have your starting position from the gap analysis you can define your strategic objective, timeframe for meeting it and the resourcing required. This will demonstrate the boards commitment to meeting the act and the level of support and oversight being provided. Compliance with the Act should be a board agenda item to ensure sufficient attention and priority is given to it. These are very important especially if you are summoned to explain the board’s actions.
Digital operational resilience testing
The Act requires financial entities to establish a program of digital operational resilience testing which may be being done already to a certain degree, documenting the range of assessments, methodologies and practices. Tests must be conducted by independent parties to ensure no conflict of interest.
ICT Risk Management
This part of the Act is very prescriptive and details some key items including:
- It requires an ICT Risk Management Framework including strategies, policies, procedures, ICT protocols and tools to protect ICT assets including software, hardware, servers as well as premises, data centres and sensitive designated areas to protect ICT assets from risks including damage and unauthorised access or usage.
- The Act is also very clear that the management body is ultimately responsible for ICT Risks . No longer is this an IT responsibility – it sits firmly with the management body.
- ICT risk should be managed by a control function – independent to ensure no conflict of interest.
- The ICT risk framework will detail how it helps meet the business strategy and objectives.
- Risk appetite and tolerances to be documented and monitored.
Incident Reporting
The Act requires financial entities to report major ICT-related events and major operational or security payment-related incidents. This implies that financial entities need to have the ability to capture and record incidents, classify them and have the necessary processes in place to inform the relevant authorities. This will require clear roles and responsibilities that need to be regularly communicated to staff, probably as part of awareness training.
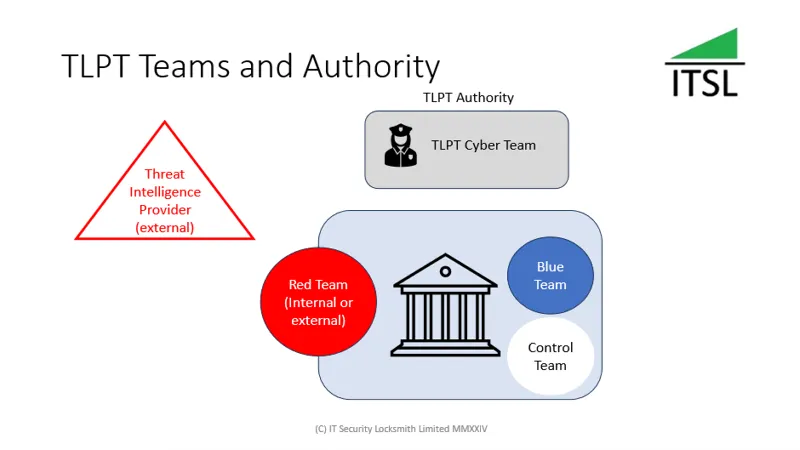
Threat-led Penetration Testing (TLPT)
Threat-led penetration testing is a requirement of the act at least every 3 years, in our opinion this is very generous but would recommend financial entities view this as the legal minimum and use their ICT Risk assessment to drive the frequency to mitigate risk. Threat-led penetration testing is also called Red Teaming and the Act provides some additional guidance on how the scoping should be conducted. This means for example that testing must be carried out on live production systems supporting several or all critical or important functions.
For more on TLPT please see our article below.
Third Party Management
Arguably, a quarter of the act covers Third Party Management, most of which covers how regulators will oversee critical third party providers. The remainder details the need for financial entities to conduct preliminary assessments of ICT risk and key contractual provisions for all third party services.
Third Party Management, Articles 30 to 44 are very important not for financial entities themselves but their service providers. If a service provider falls within scope of the Act then the level of oversight and inspection is significant. This addresses the concentration risk issue and the need to hold those service providers to account if they undermine the stability of the EU financial system.
For more on Third Party Management please see our article below.

Information and Intelligence Sharing
The Act makes provision and encourages the active sharing of cyber threat information and intelligence between financial entities. The information includes indicators of compromise, tactics, techniques, procedures, cyber security alerts and configuration tools. Interestingly there’s a requirement to report participation in information-sharing arrangements or when they terminate.
Other requirements
The other requirements in the Act should be allocated or identified as impacting specific disciplines such as ICT Risk Management, Information Security Management, Business Continuity etc. These requirements can then be factored into the next version of their supporting documentation and tracked to implementation and testing.
If you are interested in a discussion on this subject why not catch up on my talk with Chaleit.
Conclusion
Overall, we think this Act is well written and thought out. It pulls together a diverse range of resilience requirements that are the responsibility of various teams in financial institutions. It is going to take a lot of coordination and effort to implement it and demonstrate compliance. When in place it should be straightforward to maintain and result in a more robust financial market for the EU.
How can IT Security Locksmith help?
IT Security Locksmith are experienced in IT Resilience & Cybersecurity and can assist with adapting to many requirements in the new EU Digital Operation Resilience Act. We provide consulting services relating to:
- Providing board level training on Dora
- Carrying out a gap analysis against the Act
- Updating or creating the Internal Governance and Control Framework required to support the Act
- Establishing the Digital Operational Resilience Strategy and Testing Programme
- Supporting Threat-led penetration testing
- Recommending Threat-let penetration testers
- Reviewing and revising other IT or cybersecurity documentation
If you need help adapting to the new EU Digital Operation Resilience Act please email: contact@itsecuritylocksmith.co.uk.
#OperationalResilience #BoardLevelGovernance #TrustedAdvisor #EUCyber #DigitalResilience #ICTRiskManagement



