Cybersecurity critical controls
A short article covering Cybersecurity Critical Controls - ideal for small and medium sized companies looking to improve their cyber security posture.
For companies struggling to make sense of cyber security a good place to start is SANS (www.sans.org). They have a wealth of information for you and most of it is free of charge. The challenge with such a site is where to start?
SANS 5 ICS Cybersecurity critical controls
To help you we would recommend the five ICS (Industrial Control System) Cybersecurity critical controls (The Five ICS Cybersecurity Critical Controls (sans.org)). The approach is not only useful for ‘industrial control systems’ but we think is a good place for small and medium sized enterprises to start.
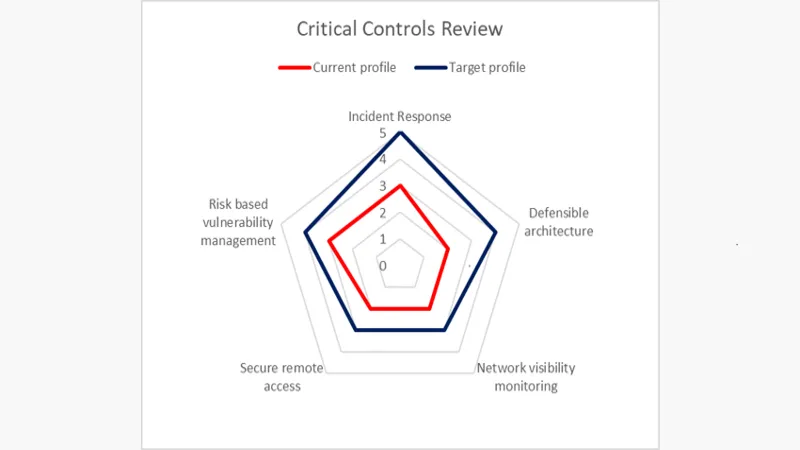
There are only five areas, which makes this straightforward:
- Incident response
- Defensible architecture
- Network visibility monitoring
- Secure remote access
- Risk based vulnerability management
We like this approach because it’s simple, easy to understand and most importantly practical. Other approaches in our opinion may be appropriate if you have a large corporation, big teams or other regulatory pressures but for the majority of firms a more practical approach is both efficient and cost effective. It is worth noting that these controls should be viewed as a minimum baseline and that most firms should comfortably exceed them in order to manage their cyber security risk.
Incident response
Incident response involves developing various scenario plans for the different types of incidents that you may reasonably expect to experience. You can start with two or three and develop more from there. Once you have the scenario plans it’s worth running a tabletop exercise to see how the plan worked. This is best run with an independent firm like IT Security Locksmith so that issues can be recorded to form the basis of an unbiased improvement plan. This initial stage informs the following stages and helps define your requirements.
Defensible architecture
A defensible architecture includes comprehensive asset identification especially important and critical systems, segmented environments for enhanced security, controlling direction of traffic, air gapped systems, network traffic collection and log collection. A final requirement is the ability to go into a ‘defensible cyber position’ which means only essential systems and connectivity is permitted. All other systems and communications being prohibited. This allows you to lockdown your systems and networks when you are under attack and are forced to take action.
Network visibility monitoring
In order to manage an incident it is critical to have actionable information at your fingertips. There are various levels of network visibility and this will vary according to your cyber security maturity. The features you are looking for may include:
- Passive monitoring – to work with most systems
- Asset inventory and tracking
- Communication protocol identification
- Vulnerability identification (and prioritisation)
- Threat detection – linked to attack groups for attribution
- Data collection and aggregation to support investigations
These features may be provided by one or multiple systems such as log collection, endpoint detection and response (EDR), security incident and event management (SIEM) and threat & vulnerability management (TVM).
Secure remote access
Attack groups target remote access systems and it is critical that they are secured at all times. This includes configuring them securely, patching them regularly and ensuring that you have strong authentication for all access requests. It is essential to monitor for vulnerabilities affecting remote access systems and having comprehensive monitoring.
Risk based vulnerability management
This is the final step and involves the continuous monitoring and triage of vulnerabilities to ensure the most important and critical systems are as secure as possible at all times. In some environments especially those with safety systems change and release management is paramount. It is essential that addressing cyber security vulnerabilities does not introduce safety critical risks or cause safety related incidents. That is why Vulnerability Management needs a collective response from all teams managing operations and can not be handled by a single team in isolation.
IT Security Locksmith services
If you like the sound of this approach why not give us a call? We can advise what's involved to conduct an initial review. We can then show you where you currently stand in each of these areas and develop a roadmap to improve your cybersecurity posture. How fast you can adapt is driven by you and the resources at your disposal. We can also help you with updating your current processes and systems to meet your target profile.
About IT Security Locksmith
IT Security Locksmith specialises in board level training and consultancy.
To find out more about our capabilities please click here.
Our services page showcases the types of services we offer.
Click here to contact us for a no obligation initial consultation.
