Are you Phishing Blind?
If you think you are ‘phishing blind’ then this article is for you and has some techniques to help you recognise and minimise the risk that others perceive automatically.

Within most organisations there are small groups of people that are ‘phishing blind’. These individuals are unable to identify the threat before it’s too late and they have clicked the link or opened that irresistible attachment. These individuals have received the phishing education but still open the emails, click links and open attachments. If you think you are ‘phishing blind’ then this article is for you and has some techniques to help you recognise and minimise the risk that others perceive automatically.
The phishing risk
Phishing is the primary vector for cyber criminals to target individuals and companies. This means it’s the initial point of compromise that then allows attackers to move within a company’s network and ultimately take full control. In most circumstances the objective is to steal data, company secrets or financial information that can then be used to extort a ransom. In most cases this manifests itself as the deployment of ransomware on the servers where the data was residing, backup systems and then ultimately workstations so that the attack is highly visible.
Cyber Security Phishing Tests
The Cyber Security team in most companies will be carrying out phishing tests and should be reporting to the board. Many of these companies will have persistent offenders that the Cyber Security team really struggle to either educate or help. The Cyber Security team has given the training more than once but the message doesn’t seem to having the desired effect.
This results in the Cyber Security team being viewed as the threat and not really helping. This I think is a little unfair because all they are trying to do is to defend the company from cyber attack and in particular ransomware which is potentially an existential threat to most companies.
Techniques to help tune into the threat
As most companies are using Microsoft the following techniques focus on Outlook and the Microsoft technology but other technologies provide similar functionality and the lessons can be applied.
Avoid using Mobile technology for emails
When using technology the email software displays a different amount of information depending on the size of the screen available. This means that on mobiles some information is deliberately not displayed because there’s no room. The hackers know this and use this feature to their advantage by changing the display information to convince the reader that the email is legitimate.
The two emails below were sent from the same email address. All that was changed was the display name. The email at the top did not come from Sherlock Holmes and I could have put any name I wanted. Which is the point, there’s no verification or checking here and the screenshot below shows you what it looks like on a mobile. This is shocking when you see it for real.
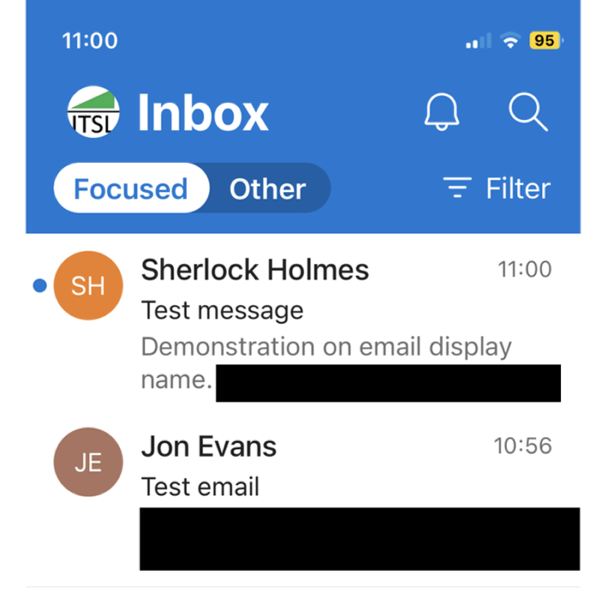
The same emails are displayed below on the desktop and clearly shows you the originating email address. This makes it much more difficult for an attacker to trick you when you are working on your desktop!
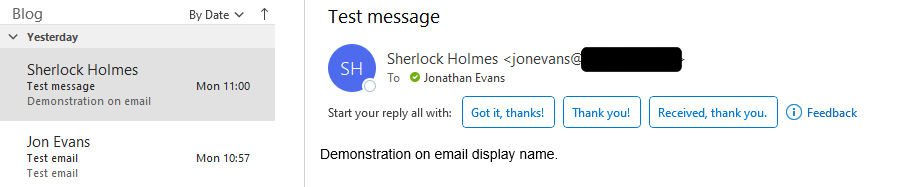
If you are ‘phishing blind’ then not using the mobile client will reduce your susceptibility to this attack vector.
If your Cyber Security Team has implemented an “External” warning on emails originating from outside your company only open them when you are using your desktop Outlook client.
Use the Outlook rules
Within the Microsoft Outlook desktop client there is functionality that can process emails on arrival. This means that you can configure rules using a simple tirage mechanism.
As an example my triage rules are as follows:
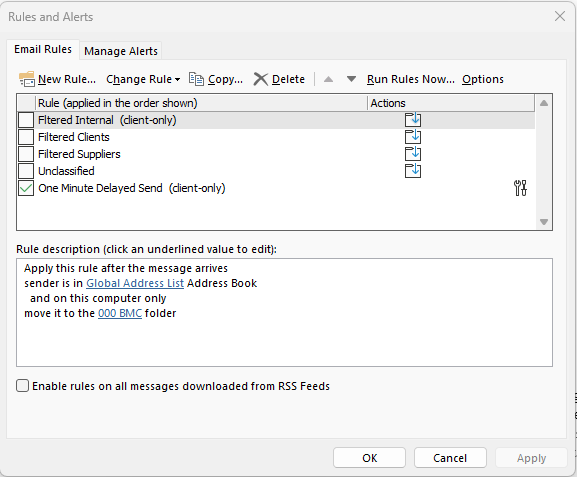
a. Move new mail from internal senders to ‘Internal’ folder (and leave as unread)
b. Move all new mail from suppliers to ‘Suppliers’ folder (and leave as unread)
c. Move all new mail from clients to ‘Clients’ folder (and leave as unread)
d. All other mail move to ‘Unclassified’ folder (and leave as unread)
This simple method now helps you think about those that are unclassified. They may look trusted but for some reason they’ve not been filtered which means there some thing potentially suspicious about the emails.
The Outlook rules are found on the Home banner, you may need to select the three dots … and it’s under Rules and Alerts.
When creating the rules I used the following:
1) Selecting Internal is controlled through ‘Sender is in Global Address List Address Book'.
2) Client and Suppliers are selected through senders address with the @domain.com only.
3) Unclassified does not filter but simply moves the emails to the desired folder.
4) The order here is very important and you can change the order by selecting the rule and pressing the up and down arrows accordingly.
The final rule is my one minute delayed send (defer deliver option) that I have enable for all outgoing emails. This is just in case I make a mistake and need to get the email back quickly before it goes to the wrong recipient.
The key benefit of this process is that all the phishing attacks land here including those from your Cyber Security team!
Use the junk mail to block repeat offenders
One of the reasons people click on links is due to a lack of time or a sense of rushing. Another way to reduce the number of emails you need to look at is to block those that are not wanted. To do this select the message right click it, select Junk and “Block Sender”.
If you find this useful you can add the button to the ribbon at the top of the screen. You can do this from within Outlook > File > Options > Customise Ribbon. Then change ‘Popular Commands’ to ‘All Commands’ and select ‘Block Sender’ from the alphabetical list.
Use the reporting button or asking for help
The approach above means that you now have a smaller set of potentially harmful emails that you need to review more carefully. If you have any concerns, doubts or think something is harmful simply report it as a phish to your cyber security team (if they have set up a button for you) or your Service/Help desk. They don’t mind you reporting potentially suspicious emails especially if it prevents a cyber attack that they need to clean up after.
Other sources of information.
Here are some useful links for more information on phishing.
National Cyber Security Centre
https://www.ncsc.gov.uk/collection/phishing-scams
Knowbe4 (security awareness company)
https://www.knowbe4.com/phishing
Cofense (email security company)
https://cofense.com/knowledge-center/how-to-spot-phishing/
Conclusion
I hope that you have learnt something and maybe you can use some or all of these techniques to help limit your phishing blindness.
Good luck with the next Cyber Security phishing test!
