Anatomy of a Phish
IT Security Locksmith analyse a phishing attack email.
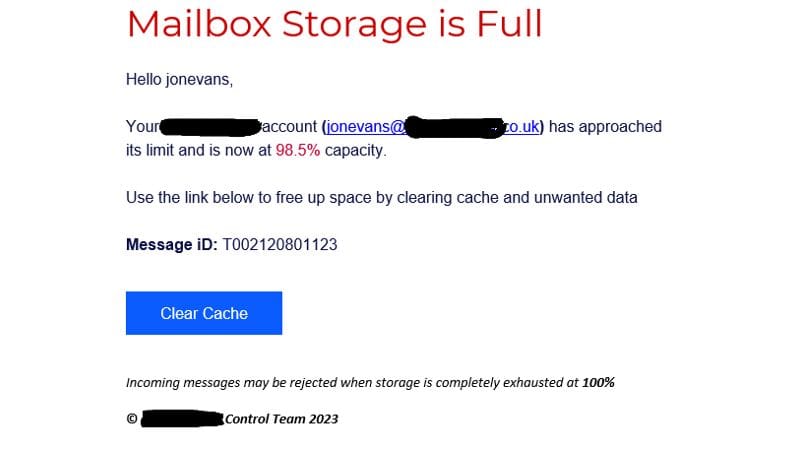
IT Security Locksmith take a closer look at a specific phishing email recently received, to help you understand where it came from and to determine if it is legitimate (hint: it's not!).
I have redacted some information for privacy and confidentiality reasons.
What makes this email a phish?
The graphic above of an email is taken from a real phishing attack email. It's an example of a good quality phish, in IT Security Locksmith's opinion, and is likely to have caught a number of people out. Email is very important to most people which means a large number of people may be tempted to click the link. The heading is very prominent in red and large font, there is a degree of urgency which is reinforced with the 98.5% full indicator and there's a threat of loss of service. All these features should be red flags for a potential phish.
What is an email header and how to access?
Simply put, an email header holds the routing information for the email and record where the email came from and the systems on route. It contains a wealth of information but you need to know where to look.
In this article I will cover Microsoft Outlook but other email packages have similar functionality.
If you have the email open (being careful not to click any links) select 'File' at the top left
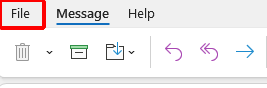
Select 'Properties'
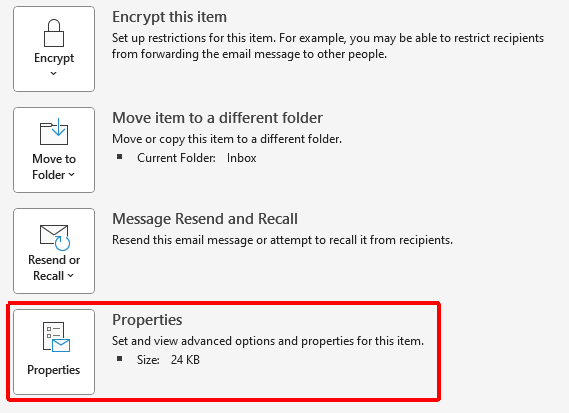
The header information is then at the bottom
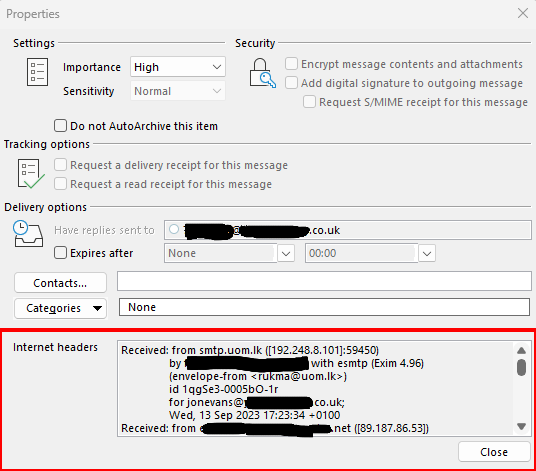
What can you do with the Header information?
Once you have selected the contents of the 'Internet Headers' (CTRL+a followed by CTRL + c) you can then paste it into a suitable header analyser. IT Security Locksmith use various systems for analysis, one of which is the Google Admin Toolbox Messageheader.
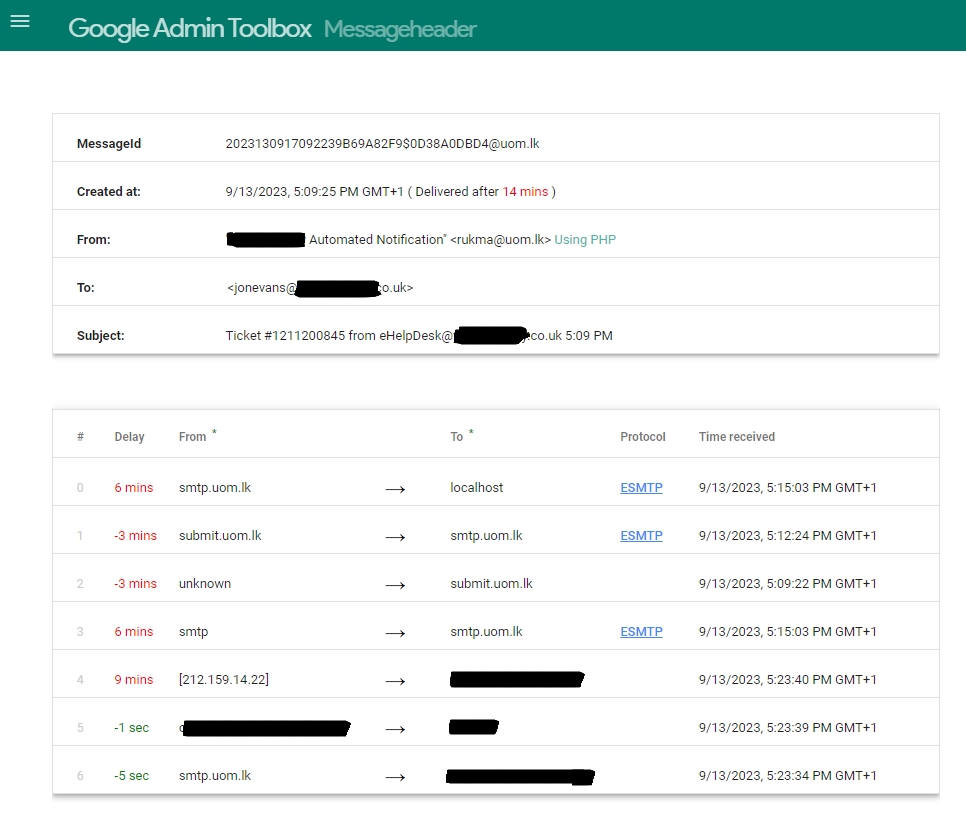
MessageHeader suggests that the email originated from uom.lk. It is important not to connect to the domain directly as it may be malicious but a simple google search reveals that this is the University of Moratuwa in Sri Lanka. This may indicate either one of their students is mis-using university resources, conducting some sort of phishing test (as a project) or that the University has a cyber security issue.
What about the link?
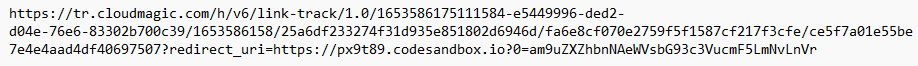
When you hover over the button in the email you are presented with the link above. But this doesn't really help that much. Performing some analysis using urlscan.io it is possible to see that this URL actually points to somewhere completely different hosted by alterVista.
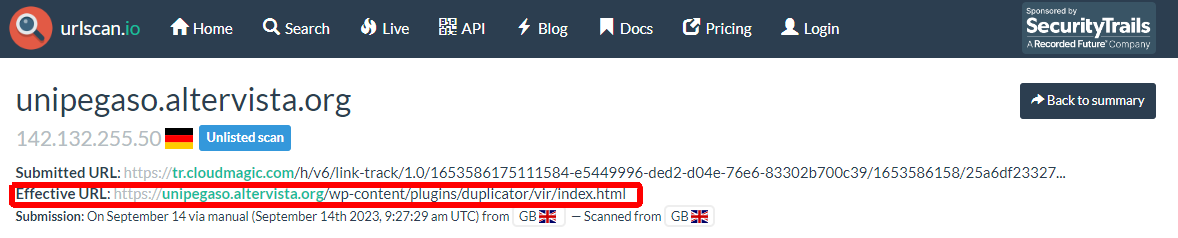
Urlscan.io also provides a screenshot of this effective URL.
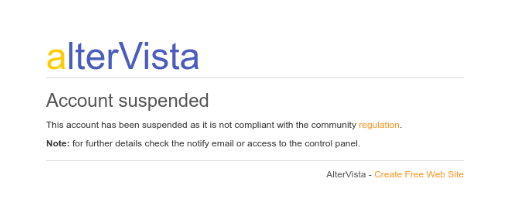
As you can see alterVista are one step ahead and has already closed this account down! Great to see that this phishing vector has already been terminated. Great job alterVista!
Final words
IT Security Locksmith hope you have found this article useful. If you have, please subscribe to the blog and share this article!
